Articles, Whitepapers
All about SSL key logging
2 min read
In CloudShark 2.5, we added the ability to use SSL key log file data in order to decrypt SSL streams in the packet viewer. But what exactly is an SSL key log file, and how do you get them so that you can do web site and web service debugging?
A key log is a log of the values used by your web browser to generate TLS session keys. Your browser does this every time, but it doesn’t do anything else with those values once they are used. However, recent versions of Firefox and Chrome will output these values to a text file with a little bit of work.
These browsers happen to check to see if there is a particular environment variable, SSLKEYLOGFILE, set up on your system to point to a text file. In Linux, this is fairly straightforward, but you can find your environment variable setup in Windows by going to Control Panel->System->Advanced->Environment Variables. Once set, the browsers will write the key data to the log file.
If you’re trying to grab this data using command-line calls, the openssl command-line client is also able to generate a keylog.
Once you have this data for a given session, you can use it in CloudShark to decrypt the SSL session. Rather than using an SSL key that you have uploaded using CloudShark’s RSA key repository, just click on the “Client SSL Keylog” button when setting up decryption rules:
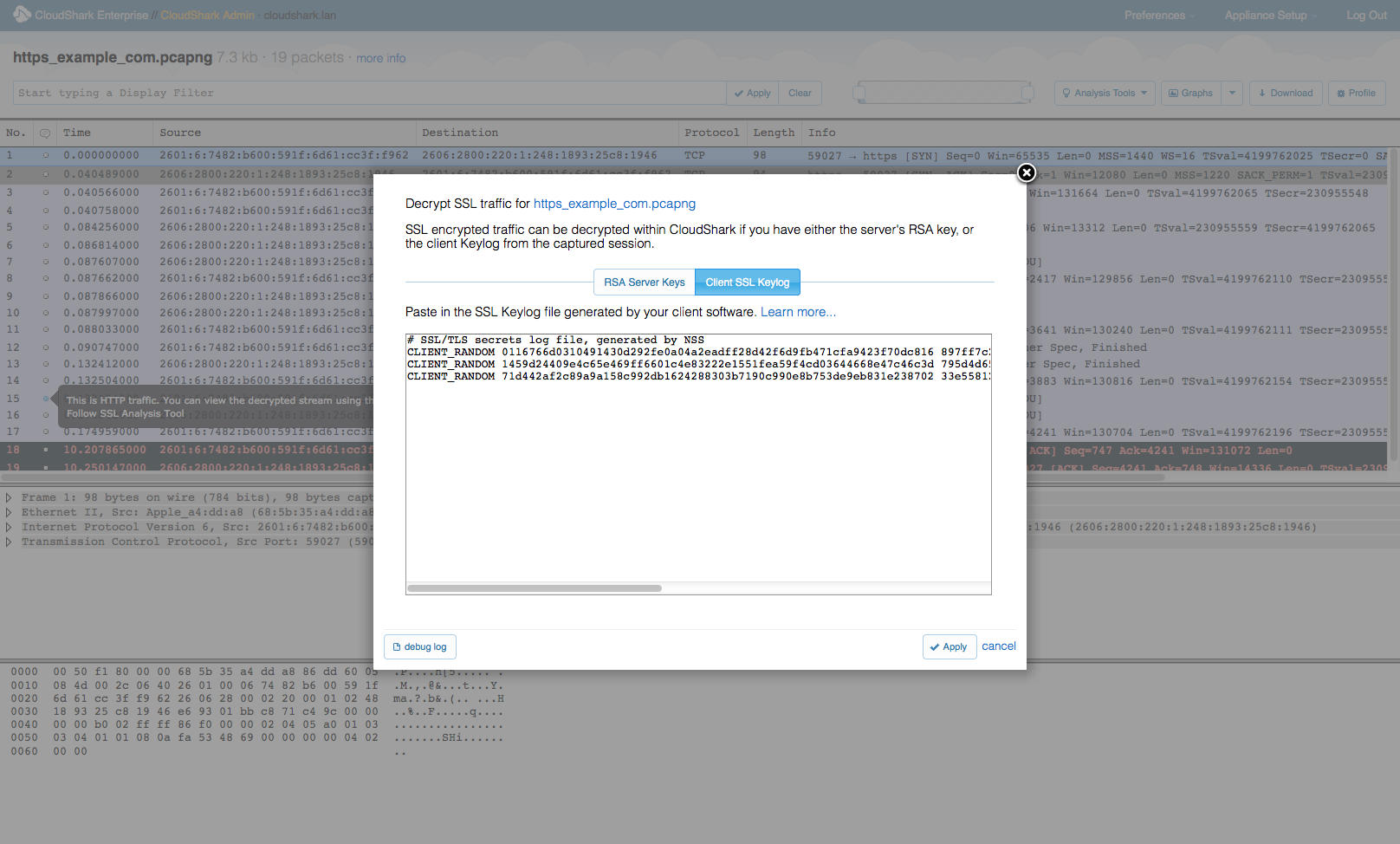
Click “apply” and you should be able to view your decrypted SSL stream.
That is unfortunately a lot of steps to do this, and with more and more web services using secure transport, it would be nice if browsers made this simpler to ease web testing. One can hope!
You can learn more about this phenomenon here from SANS.org.
Want articles like this delivered right to your inbox?
No spam, just good networking