Articles
Accelerate Network Problem Solving with Saved Filters
6 min read
Collect helpful and frequently used display filters to jump-start investigations and shorten your analysis time.
Display filters can make the difference between being overwhelmed by a PCAP, and zeroing in on what matters most. They provide a way to change which packets you see. Their powerful and comprehensive syntax makes them very flexible, but it also means they can be difficult to remember and lengthy to enter every time.
The Expert Approach
Instead of typing the same filter expression every time you need it, do what the professionals do and save your favorite display filters as part of an analysis profile. You can then apply them over and over again with the click of a button.
As network analysts, we often repeat patterns or follow specific playbooks when investigating an issue. Improve your resolution time by storing those frequently used filters and expressions. When it comes time to use them, it should be as as easy as flipping through your favorite radio stations as you drive along.
Build up your analysis profiles
In our recent webinar we showed how Analysis Profiles can provide a huge head-start when starting your analysis. Take it one step further by collecting the display filters you use most often.
Radio Presets
Think about your car radio: You don’t want to hunt around for your favorite stations each time you go for a drive. You want those presets ready to go at the push of a button! Saved filters are those presets you know you’re going to want to use down the road.
No typing required
Having the best filters defined ahead of time and available to use whenever you are doing analysis is a game changer.
Most analysts find themselves solving the same network problem over and over again. Slowdowns - is it the network or the application? Malware - where did this rogue EXE download come from? DNS - how do I find which requests and responses are causing problems? Each of these scenarios are great examples of different profiles to create, and within them, display filters to save so you won’t have to redo the work of building them every time.
Quickly scan for known patterns
We still love to scroll through a capture file to get a “feel” for what’s going on in there. It makes us feel like we’re in the Matrix. Sometimes patterns can emerge that way. Other times, there is simply too much data to do that efficiently.
For example, when troubleshooting TCP there are some repeat offenders that we might want to scan for when we first open the trace file: big delays, retransmissions, “bad TCP”, and zero-window situations are all common things an analyst might check for at the start of the session. Instead of having to type (and remember!) each individual filter expression, we can build up our filter menu with these and simply click to apply.
Uncover critical packets
Some protocol display filters like tcp or udp are easy to remember, but if we are looking at Wi-Fi, keeping tabs on all the specific packet subtypes gets a lot trickier.
Creating a saved filter to show only Management Frames means you only need to look up the syntax once! If you’re looking for “Null QoS Data”, what wlan.fc.type_subtype is that? Instead of Googling every time, save the filter for that expression to your Wireless profile!
Things can get even more complex in the world of threat-hunting where often times a Regular Expression is being used to search for a specific payload. After you have spent the time building up the filter expression, save it to your Malware Traffic Analysis profile and save yourself (and others) the work the next time.
Save protocol-centric filters with your profiles
When you load up a trace to debug something like a Samba issue, it might have extra packets in there depending on how and where it was captured. As part of the Analysis Profile you use, save a display filter to quickly filter out any packets that aren’t SMB or SMB2. You can also save protocol specific field filters to look for things like errors, lock status, requests and responses.
Filter out all the noise
Another helpful filter is one that hides all the “noise” and lets you focus on the protocol you’re debugging. Packets for protocols like ARP, NBNS, DHCP, LLMNR, etc. can all contribute to a very busy capture file when we’re looking for something else entirely!
Build and save a “no noise” filter to hide a lot of these protocols, you can quickly eliminate unnecessary packets that may be clouding your view. From there, you can export to a new session without the noise.
Jump-start analysis for others
As you are sharing captures with others on your team, or setting up profiles to be applied on import, adding saved filters will provide newer analysts a “jumping-off point” to start their investigation. Creating some common filters to specifically help other team members get their heads wrapped around what’s going on in a trace file will help improve their skills. Experts alike rely on saved filters to get to what they’re looking for quickly and easily.
Share and Report
Lastly, when sharing and reporting your findings, consider all the times that more than one thing might be happening within a trace file. By creating a session profile with a series of saved filters, you can walk others through your results by having them view each saved filter expression. Combined with annotated packets, this can be a powerful way to present your results.
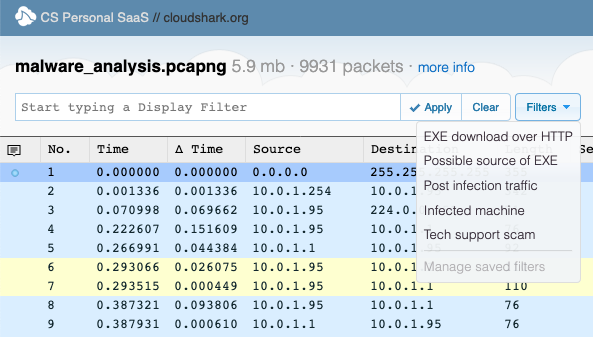
Click the image to explore this capture in CloudShark
Check out what we mean by looking at this capture. Open the Filter menu and click through each entry to update the filter showing the right packets and annotations to paint a clear picture of the infection.
Stop typing and start analyzing!
Take a page from the expert’s playbook and save some of your most useful filters! This feature is available for all our CS Personal accounts, and is available in CS Enterprise 3.7.3.
Do you have any ideas for great saved filter workflows? Let us know on Twitter!
Header photo by Daniel von Appen on Unsplash
Want articles like this delivered right to your inbox?
No spam, just good networking