Articles
5 tips to improve incident response using packet captures
5 min read
Network packet captures provide the visibility and detail needed to identify and remediate attacks
As a security operations professional, you and your team are responsible for protecting your organization; recognizing valuable data assets, assessing security gaps, and performing Digital Forensics and Incident Response (DFIR). When an attack happens, the packet data that flows across the network is critical to the incident response lifecycle. Most security analysis tools provide just parts of the information that packet data contains, but having full access to complete packet capture information can drastically improve and accelerate incident response.
What is the incident response lifecycle?
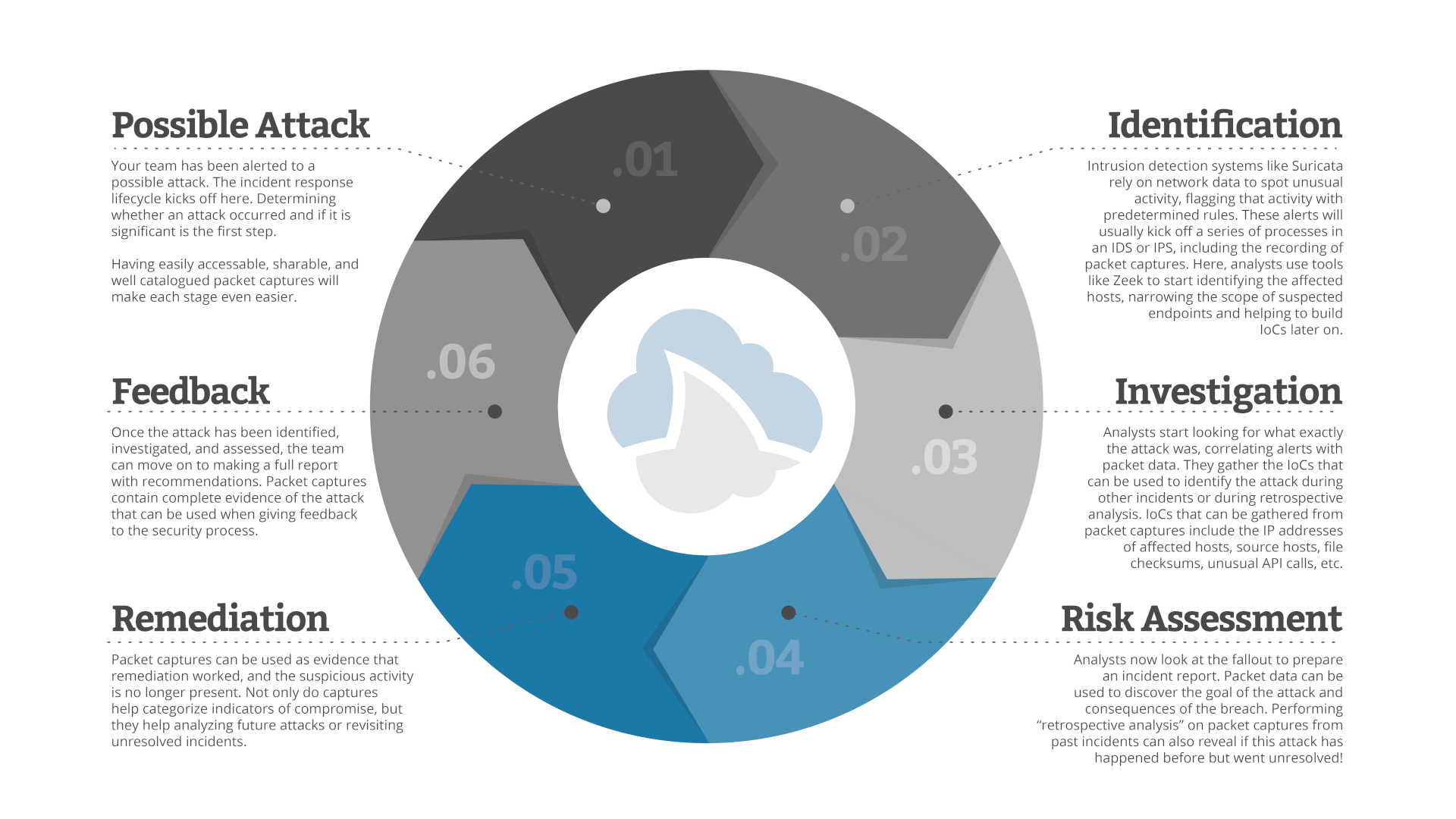
The Incident Response lifecycle is triggered when security tools, such as an intrusion detection system (IDS) or policy, indicates that there may have been an attack. When such an event occurs, your team must:
- Identify the attack to determine if the alert was legitimate.
- Investigate the attack and gather the Indicators of Compromise.
- Perform a risk assessment to determine your exposure.
- Remediate the issues created by the attack.
- Provide feedback into the security lifecycle by changing policy or writing new threat rules for the IDS/IPS (intrusion detection/prevention systems) to use in the future.
Most firewalls, IDS/IPS, and other tools that will trigger this process are able to produce network packet captures. Those packet captures play an important role at each stage of the lifecycle.
Tips for maximizing the value of packets during incident response
Here’s a few tips to use pcaps during incident response to improve your response time, increase the effectiveness of remediation, and help protect against future attacks.
Tip 1: Use Zeek to simplify investigation and help build IoCs
Zeek transaction logs are collated, organized records of network activity. Logs include every connection seen on the network, as well as application-layer information such as HTTP sessions, DNS requests and responses, TLS sessions, and more.
Zeek’s job is to narrow down the traffic you’re interested in without having to sift through mountains of network data. This makes it a great (and fast!) tool for specific incident investigation and building indicators of compromise from host, application, and service information.
Tip 2: Pivot from IDS alerts to the packets
Even when triggered by an alert, a capture file on its own is not easily tied to the alerts that are flagged by the data it contains. Have a system for correlating alerts directly with the packets that caused it.
Going directly from an alert to the packets makes it easier to generate IoCs for further analysis. Furthermore, correlating alerts with packet data lets you see everything that surrounded the attack, illuminating other related issues, deeper clues, or ruling out false-positives during identification and investigation.
Tip 3: Store captures as a history of attacks
Packet captures contain a record of everything that happens on the network. This makes them ideal for keeping information about attacks that happen over time. Keep your packet data in a centralized location that can be easily searched and accessed by your entire team.
With a detailed record of incidents unique to your organization, it’s also easy to create standard operating procedures and training for new analysts. As they level up, they can dive deeper into more complex problems curated by your team with real-world examples.
Having a historical record on your side also allows you to better understand new attacks that may be similar to past attacks. Packet captures help tell a story of attacks that might evolve or change over time, and help identify patterns that can be used to get to remediation faster.
Tip 4: Refine and re-use your IDS ruleset
With feedback from the incident response process, refine your IDS rules based on the things you learn from each attack. The IoCs you catalogued by going straight to the packets can be used to fine-tune these rules to alert you to similar attacks in the future.
After refining your rule set, run them against the captures you generated during previous attacks. The same attack may have happened before you were even aware it existed! There may have also been details about previous attacks and the scope of your exposure that your new rules can reveal.
Tip 5: Collaborate on incident data at all stages
By using a centralized system for all of your packet capture data, you can provide a way for your team to work with, annotate, and share analysis notes. Build default profiles with useful filters and views so entry level analysts and experts can easily work together. As you progress through the incident response lifecycle, you’ll be able to avoid miscommunication and repeating the same analysis steps over again.
A centralized system can also help when reporting an incident later. Being able to easily share jointly-analyzed packet data, including alert views and Zeek logs in reports will solidify your case for the steps that are taken. The ability to share captures with your team, CISO, and customers will help keep everyone on the same page and provide transparency that will help your overall organization.
Want to see more? Here’s a webinar where Tom gives a clinic of an entire incident response with an actual malware event.
CS Threat Assessment is built for incident response. Learn more.
Want articles like this delivered right to your inbox?
No spam, just good networking.