Articles
What is WPA3 and what you should test in WPA3 enabled devices
6 min read
If you’re a developer building WPA3 enabled devices or a provider looking to deploy them in your subscriber’s network, it’s helpful to know what to expect from this new security technology. CDRouter has support for testing over WPA3 protected links to help you test the scalability and stability of WPA3 links as well as the performance and behavior of applications and features on these devices.
What’s different about WPA3 secured Wi-Fi connections?
With the release of WPA3, 802.11 designers made an effort to build on the lessons learned from years of WPA2 deployments to create more secure Wi-Fi connections between stations and access points. This included the use of more advanced cryptographic techniques and new handshake procedures to reduce the effectiveness of password cracking of Wi-Fi connections. One of the biggest improvements is the use of “Simultaneous Authentication of Equals”.
Simultaneous Authentication of Equals (SAE)
One option for connecting a WPA3 protected link is with a technique called “Simultaneous Authentication of Equals” (SAE), also referred to as “Dragonfly Key Exchange”. SAE is a new 802.11 authentication method.
Using SAE, authentication is performed with a hash of a generated key that is unique to each authentication, rather than having the same Pairwise Master Key every time. This allows the AP and station peers to authenticate each other as part of the handshake process while using cryptographic tools to prevent an attacker from performing an offline password cracking scheme. The team over at Mojo Networks (now Arista) have a great video on the Dragonfly handshake here.
WPA3 SAE example
This CloudShark capture contains a WPA3-Personal handshake. We’ve annotated it to explain a bit about the fields.
Packet 2 contains the beginning of the authentication sequence. If you look at the “IEEE 802.11 wireless LAN” flags, you can see that the algorithm selected is “Simultaneous Authentication of Equals (SAE) (3)”. The “Scalar” and “Finite Field Element” parameters are values used as part of the handshake sequence based on the techniques described in 802.11.
The torrid history of Wi-Fi authentication
802.11 authentication is what allows a station to associate with a given access point and begin sending frames. Originally, there were only two authentication mechanisms in 802.11 - shared, and open. Shared authentication relied on the use of WEP (Wired Equivalent Privacy) keys to authenticate, but was shown to be very easy to overcome.
Systems using Wi-Fi Protected Access (WPA) with pre-shared keys, or 802.1X, abandoned this process, since WEP was insecure anyway. This means that they allowed any station to associate with an AP, relying instead on the *authorization* phase to prevent unwanted visitors from accessing the network itself and sending data. Authentication was revisited in WPA3 using SAE (for WPA3-Personal) and Suite-B (for WPA3-Enterprise).
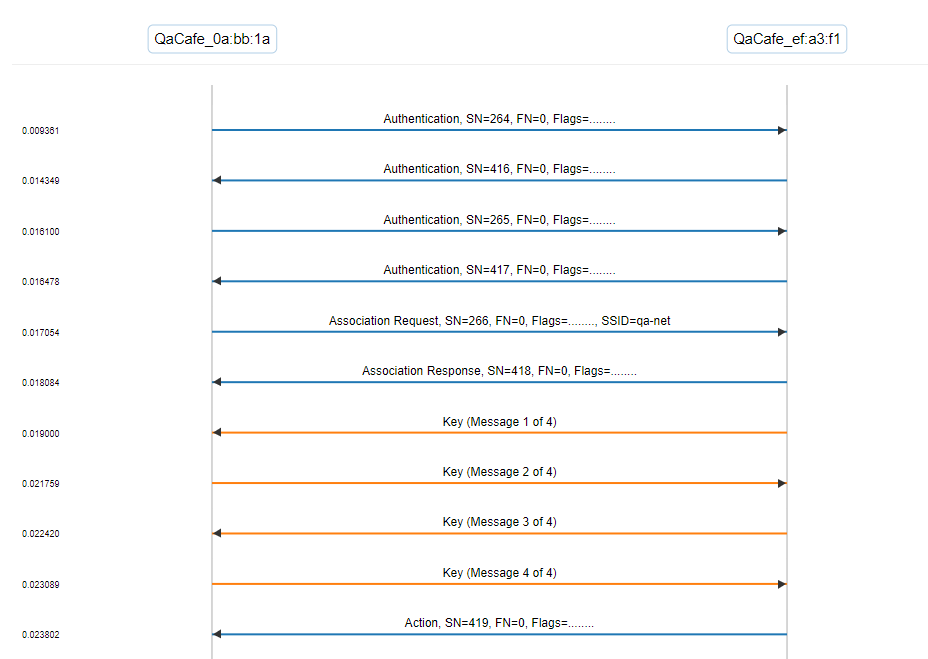
Packet 3 shows the same handshake in the other direction. Packets 2 and 4 contain the peer’s confirmation of the authentication. After this, you see the encryption keys exchanged and secured data passed between the endpoints.
WPA3-Personal vs. WPA3-Enterprise
The Wi-Fi Alliance, the group that defines WPA3, specifies a few different modes of operation for different deployments. These modes include different minimum requirements for different 802.11 features.
WPA3-SAE mode - A type of WPA3-Personal that requires the use of Protected Management Frames (PMF).
WPA3-SAE transition mode - A type of WPA3-Personal that requires an endpoint to be capable of using Protected Management Frames (PMF), but not required, in situations where both WPA3 and WPA2-PSK are enabled on the same endpoint. In this case, attempts to use SAE are rejected if PMFs are not used.
WPA3-Enterprise 192 bit mode - This is the mode used when 802.1X systems are used for authorization after association. WPA3 specifies 192 bit mode for Enterprise, requiring PMFs and limiting the EAP cypher suites that are allowed to be used. WPA3-Enterprise also uses an association mechanism called “Suite-B” rather than SAE.
CDRouter and WPA3
CDRouter’s support for testing Wi-Fi devices over WPA3 connections has a robust “swiss army knife” of functions available to match your configuration and to exercise all of the available options. This includes:
- Support for Protected Management Frames
- Support for Suite-B in addition to SAE
- Support for 256 bit pairwise and group cyphers
- Support for WPA3 in both client mode and AP mode
With these options, what things should you test on your WPA3 enabled devices?
Validating performance effects of WPA3 implementations
Though throughput and latency testing tends to be very broad in scope, any new connection technology can affect performance. CDRouter’s testing is specifically designed to see how a device’s performance changes in the face of configuration and code changes. If your WPA3 implementation and overall firmware creates memory leaks or memory fragmentation, it can cause serious performance degradation over time.
Feature and stress testing
While there are plenty of ways to examine Wi-Fi behavior and its affect on user experience by testing things like DNS, security, and application latency, CDRouter contains a wifi.tcl test module that specifically exercises Wifi association in a number of ways. These tests can apply to any Wi-Fi AP using a number of different technologies, including those secured with WPA3 connections.
Wi-Fi client restart
Disassociation and association may behave differently in each device depending on the order in which the address assigned with DHCP is released, if at all. The first three tests in the CDRouter wifi.tcl exercise this in three different ways:
- disassociation and association when the address is released and renewed (also called “graceful restart”)
- disassociation and association when the address is not released, but DHCP is restarted on the station
- disassociation and association when the address is not released, nor renewed
Given the stateful nature of these systems, a DUT may arrive in a bad state depending on the order in which these are done.
Wi-Fi association stress testing
The meat of Wi-Fi association testing comes from performance - can a Wi-Fi router or AP sustain repeated disassociation and association at high frequency? As we like to stress in our other performance related tests, repeated, normal protocol behavior may be slowly generating memory leaks or other issues that will cause a DUT to eventually fail in sometimes catastrophic ways.
Testing the base functionality of your Wi-Fi implementations overall, in addition to physical layer testing, is key to ensuring you’ll have robust products for your customer or end user.