Webinars
How do you test TR-069 enabled devices?
3 min read
If you’re developing a device or deployment that uses the CPE WAN Management Protocol (TR-069), like managed Wi-Fi or other services, what should you test for? What are the benefits of automating it with a dedicated test platform? What are the benefits of getting certified or asking your vendors to certify?
Basic components of TR-069
If you’ve been through our TR-069 training series, you’ve seen an in-depth look at all of the pieces that make CWMP work.
CWMP Endpoints
When testing TR-069, there’s a many-to-few relationship between the number of device (i.e., CWMP Endpoint) implementations and the number of ACS implementations. There are also a significantly larger number of requirements and functionality that need to be exercised on a CWMP Endpoint than on an ACS. For this reason, when we talk about testing TR-069, we’re talking about these endpoints:
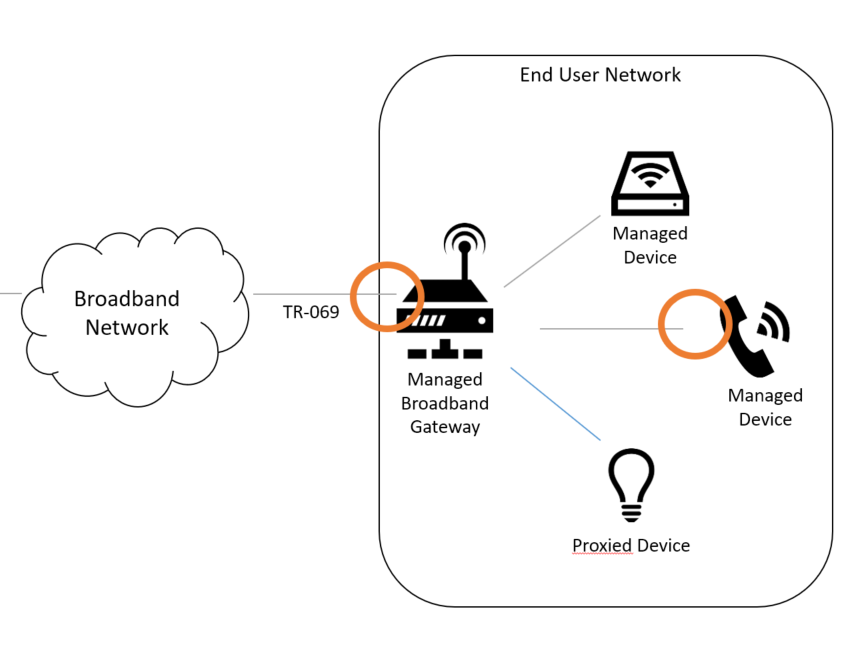
This includes broadband gateways/CMs terminating a WAN connection, home routers and cable eRouters, Wifi APs, set-top-boxes, etc. These devices might use different aspects of the CWMP data model, or may not have a direct connection to the Internet, requiring special mechanisms in order to send them a Connection Request.
Protocol stack and underlying system
The basic protocol stack of TR-069 is straightforward, but in addition to the stack definition is the underlying application that “hooks into” the device’s components through the CWMP data model.

The device’s supported data model are the data model objects and parameters that could exist on the device, while its instantiated data model are the objects and paramters that represent the current run-time state of the device.
What should be tested?
Overall, each aspect of the protocol should be tested, including the device’s ability to actually make changes to itself when told to do so by the ACS. This includes:
- Session establishment and termination, which covers everything from establishing a TLS session and the problems that arise at that layer, validating the XML syntax of SOAP and the CWMP messages themselves in accordance with the schema, validating the initial Inform message for content and use, and the compliance of HTTP/TCP behavior.
- Connection Requests, including requests over HTTP, direct to a LAN device through STUN, and with the XMPP Connection Request mechanism. This also means testing the security of Connection Requests to avoid code injection and other vulnerabilities.
- Basic RPC functionality, covering both required and optional RPCs.
- Data model validation, including syntax and schema compliance, and real-world scenarios like Wifi configuration.
Testing with CDRouter
CDRouter is the official test platform for the TR-069 protocol. Request an evalutation to get started building better TR-069 devices, faster!