Whitepapers
Transform Your Packet Capture Workflow with these 4 Best Practices
8 min read
CloudShark Enterprise, is a packet capture repository, analysis tool, and collaboration platform that we built to solve the challenges faced in our own capture workflow. It uses Wireshark under the hood, but all you need is a web-browser.
We believe that being able to quickly share packet analysis in context, without friction, and across teams, changes packet captures from something that are too often a “last resort” to a resource that can be relied on to provide answers faster than before. CloudShark empowers your team to take network analysis to the next level.
Our Story
When there is a technical problem here at QA Cafe, more often than not it involves looking at a packet capture. Instead of waving our hands and trying to describe what we’re seeing, we go straight to the packets.
We’ve been building test solutions for network devices since CDRouter debuted in 2002. Over that time we have learned that the sooner you can put a trace file of a problem in front of someone, the sooner they’ll be able to give you an answer about it. Network data doesn’t do well in the abstract - you need to look at the packets!
CloudShark Enterprise grew out of our own need to manage and communicate around network capture files. By prioritizing sharing and collaboration you can make network problems easier to solve in less time.

1. Keep all your important captures together and organized in one place
Packet captures can come from anywhere in your network. They can be captured on span ports, taps, firewalls, IDSs, web servers, desktops, wifi access points… the list goes on and on. It can be overwhelming dealing with files from so many different locations. Often they get dumped into a folder with a hope that you’ll be able to find it again. You end up with file names like “whatever.pcap” or “whatever-2.pcap” not to mention the less-than-helpful “20181031142033.pcap” Was there anything important in there? No doubt. Confidential? Probably. Without a system in place, there’s no good way to keep track of them all.
Worse, is when a situation comes up that you are sure has happened before but can’t find the trace file from last time. The same goes for when you’re looking at a specific issue with a vendor, and they ask to see all the other related traces from a different system. Or you do find a single file with 2 GB of data, but without any notes or write up of what happened.
By keeping any important PCAP file on a central server, it gives your team a single place to look whenever we need to find something. Everybody should be able to access it through a web-browser, and features like sorting on metadata or searching on packet data should be fast and intuitive to do.
Use tags to organize files. Different approaches work for different teams. Tagging where a file comes from, or grouping them by trouble-ticket number, vendor information, or even datacenter location will make files easier to find, and harder to lose. In a large network, with frequent packet captures, the easier it is to find a file, the better.
Don’t forget to back-up this archive! That way you’re not worried about losing data if a disk crashes or a laptop goes missing. An additional feature to consider is being able to automatically clean up files after a certain amount of time. Most places have a data-retention policy in place for certain kinds of data. You shouldn’t have to worry about things slipping through the cracks.
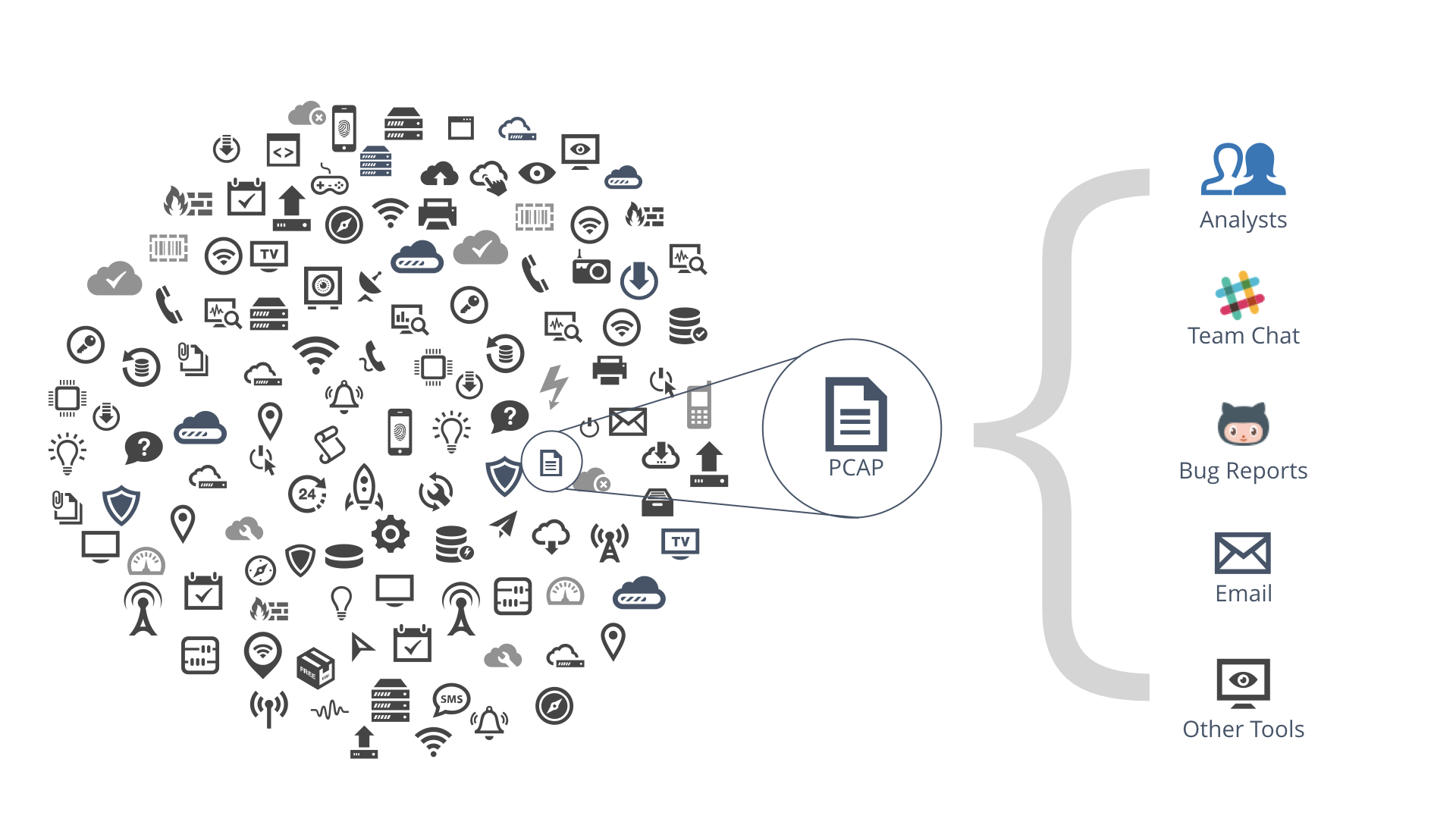
2. Make Looking at Packet Captures Easy for Everyone
Why aren’t PCAPs used by everybody all the time? Well, it’s true that they’re complex, technical, and require a lot of knowledge to analyze. But beyond that they’re often very large and need to be copied to your system first. They require installing special software in order to look at them, and that makes it really difficult to share what you’re looking at with the rest of your team when you need to ask for help. No wonder people avoid them!
Gerald Combs, the creator of Wireshark, put it really well in one of his Sharkfest keynotes. Packet captures are often the last resort, when really they should be a first or second.
In order to make packet captures the first-resort method for understanding and solving networking problems, they need to be easier to look at, share, and use inside of existing communication tools.
Think about what is installed on every single modern device. The web-browser. So many other tools have moved to be “web native” and by enabling PCAP analysis in a standard browser environment, it eliminates a lot of the friction that discourages people from choosing pcaps first.
By making capture files easier to get to and view through a regular old web-browser they can be used more, and integrated fluently into your existing communication tools like email, chat, and bug trackers. The more people have easy access to the PCAP data, the more your team can use them to solve problems.
3. Bookmark your analysis for others
Too often, pcap analysis involves asking someone to look over your shoulder to follow along, or looking at screenshots of someone else’s analyzer. A picture they say is worth 1000 words, but a screenshot? By putting a bookmark in your analysis, anybody else can come along and see exactly where you’ve left off without repeating the same steps each time they open the file. This enables people to quickly jump right into the middle of any analysis.
Context is everything when dealing with packets, and looking at a screenshot doesn't provide enough of it.
If every capture file can be associated with a unique URL, go one step further and make all of your analysis tools browser-based and available directly via a link as well. When someone visits a bookmark, they are brought to exactly the same view that the sender was seeing - right down to any display filters that are necessary and including any packet annotations that have been left for them.
Imagine being able to link directly to a specific HTTP stream - already un-gzipped and decrypted, and presented to an application developer in a bug report. Are these headers correct? That developer needs a web-browser and a single click to see the specific traffic that is in question. They have everything they need to answer the question right in front of them.
Beyond that initial link, they will be able to move around within the capture file. This makes it possible for them to resolve things so much faster than if all they had available was a single static screenshot.
Being able to link directly to the data in question, and at the same time provide access to the rest of the trace file, that application developer can quickly fix their bug, and close out the ticket. We can avoid the back-and-forth, the step-by-step repeat-after-me that was required to get their analyzer to show them the same thing. It makes working with PCAP data a breeze! When a task is easy to do, it will happen more often.
4. Choose tools that play well with others
“Packets or it didn’t happen” is something we hear a lot. That means you need to get the packets in the first place! We’ve been talking about putting a system in place to make them easy to use and share, it’s critical that all of your capture tools are able to send files directly to your central server.
When looking at capture tools, look for ones that provide hooks to integrate them with management platforms. Whether you’re looking at commercial tools, or rolling your own with something like dumpcap, look for ways to get the packet data back in front of a human being. Packets don’t help if you can’t see them. This might be as simple as a post-capture command on a dumpcap ring-buffer command or as full fledged as a native capture API built into your wifi access points.
Invest the time and energy into building a network-wide capture system that is reliable and capable of zeroing in on where problems are. When something goes wrong, the last thing you should be doing is wondering how to get capture files into your analyzer and in front of a person. Find tools that push them to a central server, organizes them, and gives your team a head start on performing their analysis.
Summary: Invest in your PCAP workflow
As a network engineer, PCAP files are one of your most powerful assets. They hold vital information to debug network problems, improve performance, and secure your business information. By keeping them organized and making them easier to access and share by every member of your team, you can reduce the time and effort needed to solve problems, and speed up the resolution of any network issues that come your way.
Start a trial today and learn how we can help transform your network analysis workflow and get you and your team resolving issues faster than ever.
Want articles like this delivered right to your inbox?
No spam, just good networking.